When we start to implement MFA or Conditional Access to larger Azure AD environments with many different user types, you some times come across end-users that simply don’t have any possibility to answer a MFA Challenge. It could be production users, external users, teachers or even students in some cases that simply have no device where they can configure an MFA method.
In many of those cases a FIDO2 hardware token and passwordless would be the solution, but in some scenarios that won’t be cost effective or even supported depending on the device type and how the end-users are utilizing the device.
Instead of using traditional MFA method like Phone/SMS/Email/Authenticator Apps we could also use classic OATH TOTP hardware tokens.
I’ve received a couple of demo hardware tokens with different capabilities from the company token2, and in this blog post we will cover how to implement this in Azure AD! Thanks token2 for making this blog post possible!
The Hardware token
A classic OATH TOTP hardware token is a small device, that will generate a Time-based One Time Password (TOTP) each 30 seconds that also will fit in your keychain
In this case, we are using a classic C202 OATH hardware token from token2. I’ve used this type of device in several Conditional Access projects, deploying hundreds of them to different customers during the last years.

Specifications:
- Built-in Button, 6 Character LCD
Screen - Security Algorithm: TOTP (TOTP is based on HOTP
with a timestamp replacing the incrementing counter) - OTP Length: 6 digits
- OTP Time interval: 30 seconds
- Dimensions: 49.8 x 26 x 8.25mm
- Water resistance: IP67
- Secret hash: random – factory programmed
- Hardware Certification: RoHS Compliant
- Operating Temperature: -10°C .. 50°C
- Tamper Evident / Tamper Protection
- Battery Type: Standard Lithium Battery
- Battery Lifetime: 5-7 Years
(depending on usage)
Pre-requirements before configuration in Azure AD
Before we can start the configuration in Azure AD we have a couple of pre requirements that we need to check off
First of all, all users who will use a hardware token will be required to have an Azure AD Premium P1 license.
After you have received your hardware token from Token2, you will need to request a .CSV file from the supplier.
The .CSV file contains information such as Serial Number, Secret Key, Time interval, manufacturer and model of the hardware keys.
Since this file contains a secret key, it is important that this file is kept encrypted, at both rest and in transit.
When you request the .CSV file from token2, you will be able to use PGP encryption to ensure a high level of security.
The .CSV file will need to be modified, where you simply attach a UPN to the serial number of each hardware key located on the back of the physical key.
Importing the CSV file to Azure AD
At this stage, you have received your hardware tokens, you have requested and received the .CSV file that contains the data and secret key about each token and you have assigned UserPrincipalName to the hardware tokens you would like to activate in Azure AD.
Now it’s simply time to import the .CSV file to Azure AD to be able to activate the hardware tokens for the end-users.
- Go to portal.azure.com and sign-in with you dedicated administrator account
- Elevate your self to the Global Administrator role (The roles Authentication Administrator, Authentication Policy Administrator only works for managing and updating some parts of the configuration, but not for importing the actual .CSV file into Azure AD.
- Open the Azure Active Directory and go to the security tab

- Click on the MFA tab

- Go to OATH tokens and click on upload to select the modified .CSV file

- When the file have been uploaded, you should now be able to see the users and their assigned hardware tokens

- To verify the function of the hardware token and to activate it for the end-user, click on the “Activate” link and be ready to start the hardware token and enter the 6 digit code

- The hardware token should now be activated and ready to ship to the end-user.
The end-user experience when using OATH tokens in Azure AD as MFA authentication method
When you sign-in to Azure AD resources and faces and MFA challenge, you will simply just start the hardware token, and enter the 6 digit code as your MFA method:
- Select the “Use a verification code from my mobile app”
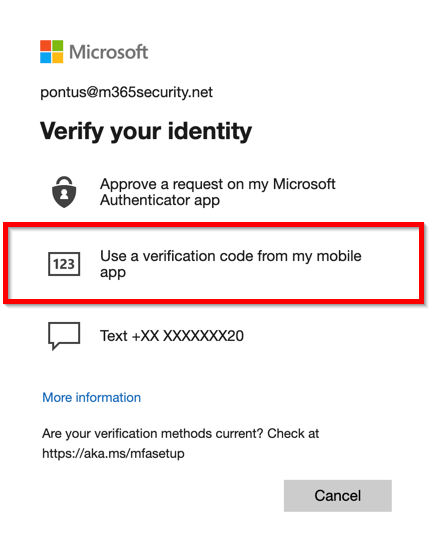
2. Start your hardware token, and enter the 6 digit code and click on verify

You have now successfully sign-in using your OATH TOTP Hardware token.
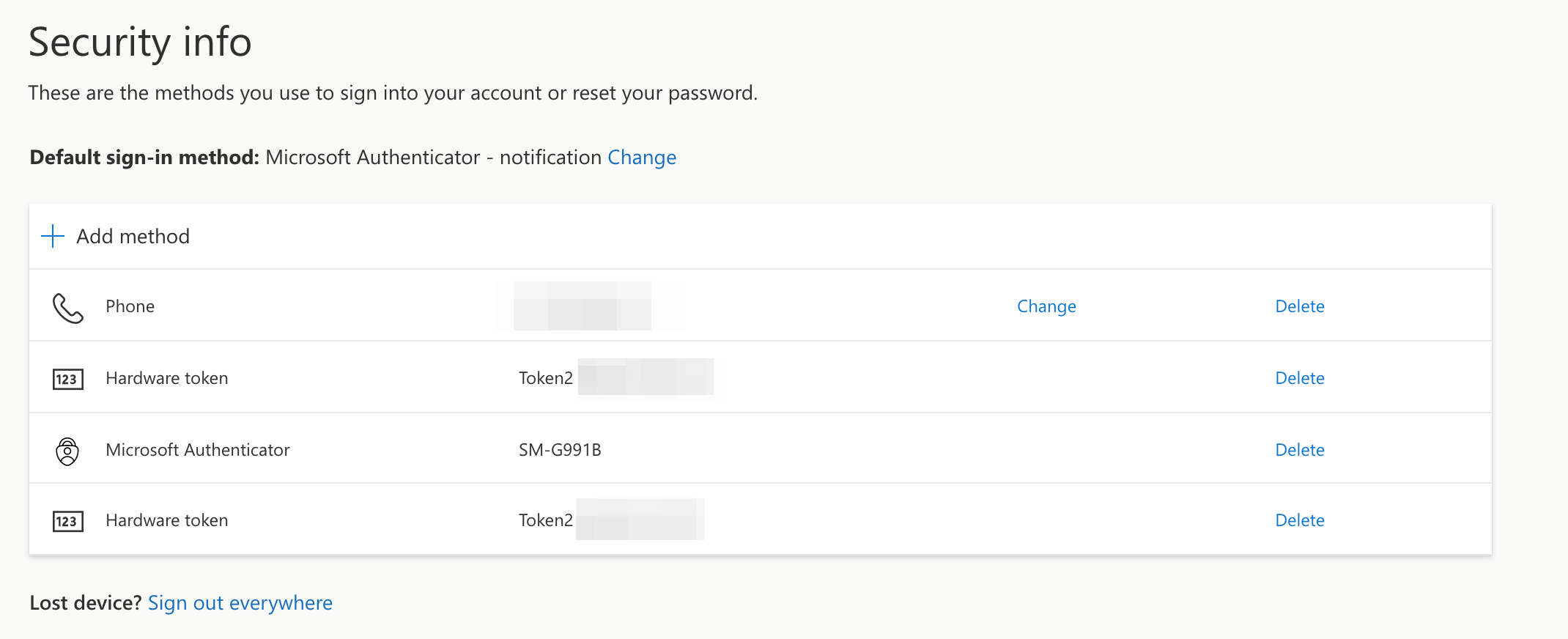
Now you might wonder, what will happen if you would like to verify your sign-in using the verification code from the Microsoft Authenticator app? It will work just fine, even if you have several OATH TOTP hardware tokens configured on the same Azure AD account.
View from the Security-info site showing all MFA methods available:
Common Q&A
Question: Does the OATH TOTP hardware tokens works with Self Service Password reset?
Answer: Yes, but depending on the SSPR configuration you might need to add several methods.
Question: Does the OATH TOTP hardware tokens works when you add a new device to Azure AD and are prompted with an MFA challenge?
Answer: Yes
Question: What will happened with the hardware token when an employee leaves the company?
Answer: The hardware token can be reused through the following steps:
1. Delete the hardware token from Azure AD
2. Modify the .CSV file and match the serielnumber of the hardware token with a new user (UPN)
3. Upload the .CSV file and verify the hardware token, the new user is now good to go.
Question: What will happend if the end-user by mistake deletes the hardware token from the security info portal?
Answer: The hardware token will automatically be inactivated in Azure AD, the end-user will need to contact the administrator that will be required to re-activate the hardware token.
Question: I’m receiving an error when I upload the .CSV file with all toke token information to Azure AD, what’s wrong?
Answer: Ensure that you follow the guidelines of how the .CSV file should be populated with data and make sure that you have the Global Administrator role assigned to your admin account when uploading the file to Azure AD.
Question: Does it work to add several OATH TOTP hardware tokens on one account?
Answer: Yes

2 replies on “How to implement OATH TOTP Hardware tokens to Azure AD”
Hello, do you know if the Global administrator right is still needed to import tokens? We would like to use RBAC role for that but it seems that it is not possible.
LikeLiked by 1 person
Hi,
Global Admin is still a requirement what I know
LikeLike